
In our previous topic, we talked about a collection of Spanning Tree Protocol features that could help to reduce the Convergence Time with a Spanning Tree Protocol, what here in this topic, we wanna talk about another collection of Spanning Tree features, this time though these features are design to helping increase the stability of the Spanning Tree, and by increasing the stability we talking about things that might help prevent a layer 2 Loop is in example, we got 4 features we wanna talk about in this topic.
The first one is BPDUGuard
And this is gonna work
typically handed hand with Portfast that we talked about in the previous
session, we gonna see this can add some extra
Loop Prevention Protection on a
port that configured for Portfast, if we accidentally plug in a Switch to that
Port, that might potentially cause a loop.
Then we gonna take a look at
BPDUFilter
And this is an interesting
one because normally we think BPDU’s are good
think they can help prevent loops but there is a time, we might want to filter
out and not send those BPDU, we will see how to do that.
Next, we take a look at Root Guard
Let’s imagine that, we
got a Spanning Tree Topology and you know that
this(SwA) is gonna be a primary Root Bridge and this(SwB) is gonna be secondary
Root Bridge, and you don’t want any other Bridges ever becoming the Root,
you don’t want somebody accidently or intentionally introducing the Switch on the network with a Superior BPDU
and try to take over the Role of the Root, well what we can do is say “if there is a switch of a specific ports claiming to be the
Root, we not going to believe that switch”, and feature that
often gonna be configured along with Root Guard, is
a LoopGuard
LoopGuard is another Loop
prevention mechanism as you might be able to guess by name but it can help us
out to situation for example where, “we have a
Unidirectional Link, that stop receiving BPDU’s from a Designated port on a
segment, that must mean it’s OK for us to go active, not necessary maybe we
have a Unidirectional link failure”, Loop Guard can help us to
protect from that.
Let’s get ride into a
discussion of first of these features BPDU Guard. BPDU Guard can work handed hand with Portfast, remember with Portfast, we can tell
an Access Port that, it should not go through the
Listening and Learning state, if the device connected to that
Port, we were essentially saying “Mr. Port, i
promise, i am only going connect End Station”, “i am not going to connect Switch or anything else that might
cause a loop”, so please don’t make, a connect device wait through 15 seconds of Listening and 15
Seconds Learning, let’s go active
almost immediately, an addition to doing that, Portfast has a Loop prevention mechanism built in,
if we have a port enabled for Portfast, and its
sees BPDU coming on that port, it realizes that it’s been lying too,
it looks like somebody attached a switch to this
port and when Portfast starts to see these BPDU’s, it can start Blocking
however, it doesn’t happen instantly,
there can be a brief time where we do have a loop, and BPDU Guard can help prevent
that, temporarily loop that we could have during that time that a Portfast,
port transitions into Blocking.
And we can enable this globally or we can do a port by port bases,
if we enable it Globally, it’s only going to
apply to ports that have Portfast enable
and we said that, what is gonna do is immediately
start Blocking Traffic, we going
to specifically go into a “Err-Disabled State” on
that port if we receive a BPDU because that Port has been configured for
Portfast.
We promised, we are not going to attach anything that should be sending a
BPDU, if we see that very first
BPDU, BPDU Guard is gonna shut that Port down, and go into a Err-Disabled State.
By the way how do you recover from an Err-Disabled State,
after you correct the issue that was causing a
problem, and the first place a way
to come out the Err-Disabled State is,
to simply some people call it, Bouncing the Port,
what i mean by that is, we go into
interface Configuration mode and we do a “Shutdown”
followed by “No Shutdown”, we administratively take it down, bring it
backup, and of the condition causing the error is
no longer there, that’s gonna clear out the Err-disabled State, if
you take a look at the topology on picture

We got port fastetherent 1/0/1, that
has Portfast enabled, and if we connect end station.
To that port great, that’s really, we intended for, we might have a Laptop with an SSD, instead of
regular spinding Hard Disk Drive, it might boot up very very quickly and it
might send out a DHCP Broadcast and if Portfast were not enabled, it might not
able to obtain an IP Address because that port is not yet active, if it’s sending
out that DHCP Broadcast, however, if we
accidently or somebody intentionally plugs in a Switch to this port that Switch
Sw5 in this case, is gonna be sending BPDU.
And which that first BPDU is seen on that port because we now have BPDU
Guard enabled that port is immediately go into an Err-Disabled State.
Now we understand the
theory of BPDU Guard, what it trying to accomplish let’s take a look at configuration of BPDU Guard.
That’s how to
enable this on interface bases but we can enable it globally, we
could say in global configuration mode.
And Verification command, we can issue is
Our Next Spanning Tree stability feature is BPDUFilter,
and normally we like BPDU, we want
BPDU’s to be exchanged between our Switches because the
BPDU’s help us to make a Loop-free Spanning Tree topology, what BPDUFilter can do is, prevent a port from
sending BPDU’s and we can enable this on a Port
by Port bases or we can enable it globally and if we enable it globally, it’s going to apply to ports that have Portfast enabled
But
the big question is when should we use this,
Cisco cautions us, we should only use BPDUFilter
when necessary, well when would something like this be
necessary, i have sketched on picture here.
A couple of different Autonomous System, remember what an
Autonomous System is, Autonomous System is simply
a network under a single administrative control, these 2 Autonomous System A and B, they could be your company and
your Service Provider if you have a Layer 2 Ethernet connection with your Service Provider
or maybe its within your Company you got 2 different Department that have their
own IT Staff, they manage their own Switches that configure the own STP
parameters but they still need to interconnect.
Well maybe you don’t want to be exchanging Spanning Tree information between
these 2 different Autonomous System, even with in the same
company, BPDUFilter can be used to do that,
BPDUFilter can be used to prevent one Autonomous
System from sending BPDU’s into another Autonomous System, and i
mentioned that we could enable this at the Port
level or Globally, the behavior is actually bit different and
its most dangerous, were in most danger of
creating a loop if we enabled this
at the Port level.
We will talk about the
distinguish when we get into the configuration in a movement, but let’s visualize
what this might do for us, if we setup the BPDUFilter may be on Switch C in an
Autonomous System A.
That port on SW C, it’s not going to be able to send out a BPDU, it’s not gonna
get down to Autonomous System B, because BPDUFilter is going to filter that out, but think about this, what if Switch D in Autonomous System B were sending a BPDU into a
Switch C, with that BPDUFilter that
we configured for Switch C, would it ignore that BPDU coming from Switch D.
Well the answer of that depends on how we configure it, do we configure it at Port level or do we configure it
globally, let’s take a look at configuration and talk about the
different behaviors that we get from Port by Port
Configuration vs Global Configuration.
First here, how we set it up at the
Port Level
Here what that
does, when we set this up the Port level, it’s very plain and simple, we telling that port do not send any BPDU’s and if you
receive any BPDU’s ignore them, and
that could be a bit dangerous because we ignoring
any incoming BPDU’s, we receiving BPDU indicating that we were connecting to a Switch and we just ignoring those, we might
get into Loop Situation, it’s safer if we enable this globally, here how we do
that we say.
And here what happened if
we enable it globally, The Switch is bit more curious, the Switch says “ if i receives BPDU’s on one of these Portfast ports that have
been globally enabled for BPDUFilter, if one of those ports receives the BPDU
that Ports is gonna lose its Portfast status, so in this case, we not ignoring incoming BPDU’s instead incoming BPDU’s their
viewed as warning, look at, we got
a Switch attached to the this port maybe we shouldn’t be on Portfast mode
anymore, and we gonna transition
out of Portfast mode.
Infect, when that port first comes up it’s going to try to seek out
and see, we have any attach devices that would be sending us BPDU’s and its gonna send “10 BPDU’s
of its own”, and if it receives
any BPDU’s in returned then it’s
going to say “No! we should not be a Portfast Port,
and we gonna transition out of the Portfast Mode”, to see if we
have a BPDUFilter enabled or not, we
can give the command.
We can see how many
BPDU we sent/received, after we enable the BPDUFilter, the
number of BPDU has been sent that should not be incrementing
anymore because we are not gonna be sending any additional BPDU’s.
###############################################################
# Take a Break of Tea/Coffee,
then we will go to next feature #
###############################################################
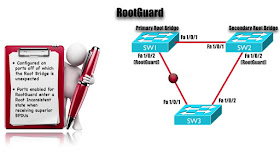
Our next feature is Root Guard, with Root Guard we want to prevent somebody from intentionally or
accidentally adding a Switch to network that might send us a superior BPDU and
claim to be the Root, for example, i got couple of Switches on
Picture.
That i don’t mine, if they become
the Root, Sw1 that’s gonna be my Primary Root
Bridge and Sw2 is gonna be my secondary Root Bridge, however, i would not want Sw3 to become the Root, and
we have enable the Root Guard on the bottom ports of
Sw1 and Sw3 to say “if i receive the superior BPDU coming into this port, we are not
gonna believe”, we gonna go into a
Root-inconsistent State, here how we set it up, we gonna configure Ports, that should not connect us to the
Root Bridge, and if we do receive
us a superior BPDU coming in one of those ports, this ports is gonna start
Blocking traffic, Specifically its gonna go into a Root-Inconsistent State.
So, let’s imagine that “Sw3 does send a superior BPDU up to Switch Sw1”,
when it (Sw1) gets that superior BPDU, it says “i
am enable for RootGuard this is a superior BPDU and i am not gonna trust that”,
instead i am going to transition this port to a
Root-inconsistent State.
Until those superior BPDU
stop, and as soon as they stop we transition out of the Root Inconsistent State,
we don’t have to administratively do anything to
recovered from that like we did with the Err-Disabled State, now
let’s see how to set this up, Root
Guard is only going to be configured at the Port
level, you would not want to be Globally enable it, but we going to strategically go into those ports, of a which
we would not expect to see the Root Bridge, here we gonna go
into interface
We would do that all of the ports, of which we would not
expect to see the Root Bridge, if we did have a port, that was in the Root-Inconsistent State, here
how we can be determined that we could say
This example,
its look like interface fastetherent 1/0/2 is in the Root-Inconsistent State.
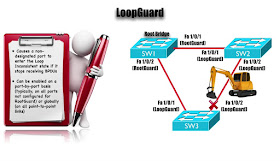
And our Final feature
that, we wanna to talk about in this topic is Loop
Guard, this is something that we want to configure in conjunction with Root Guard, what’s its gonna do is, cause a Non-Designated Port to enter a Loop-Inconsistent State
which is Blocking State, if it’s stop receiving the BPDU.
Here why we do that, normally on a network segment a Designated Port is gonna be
sending out BPDU’s and the Non-Designated port receives the BPDU’s, now this Non-Designated
Port stops receiving the BPDU’s, it’s assume that the topology is Loop free and it’s start to transition
to the forwarding State if it were Blocking.
However,
maybe its stopped receiving BPDU’s not because, we have a Loop-free topology,
may be have in one example, “a Unidirectional link,
and if we have Unidirectional Link may be, we were not receiving BPDU’s but we
can still send them”, we could create a one way Loop around this
topology however, with LoopGuard enabled when the
Non-designated Ports stops receiving BPDU’s
it transition into a Loop- Inconsistent state where it blocks traffic, and its gonna remain
that state until, it receives the BPDU and then
it automatically transitions to the appropriate state maybe Blocking or maybe Forwarding, based on that BPDU and we can enable this on a Port by Port bases, we
would probably do that on all ports that did not
have a Root Guard enabled if we were using Root Guard or we can turned this on Globally and if we turned it globally,
it’s going to apply to all Point-to-Point links.
Let’s visualize how this might help us out. On picture notice, we have a link between Sw2 and Sw3 and the port on Sw3 is currently Blocking but we know that every
network segment has a Designated Port and that Designated port, in this case is
Switch Sw2 fastethernet 1/0/2 interface and let’s say that, we have a Unidirectional Link Failure, we have
something like we talked about earlier called a
Backhoe fade, here comes big
Backhoe Fade into the network and it damaged the Fiber Optic Cable.
i am no longer
able to receive traffic from Sw2 but we can send traffic and that can cause a Loop if we did not have a Loop Guard enabled, but
we do Switch Sw3 says “i am no longer receiving
BPDU’s on this link, so i am going to enter Loop-Inconsistent State”.
Let’s see how to set this up, first
we can go into Interface Configuration Mode
That will
enable it Port by Port, and to enable it Globally we would say
And to see its enabled or
not, we can give Verification Command
And you can see the second line of output of bottom it says
LoopGuard default, it is enabled that
only can force Spanning Tree Protocol feature
that can help us increase the stability of our Spanning tree topology,
we talked about BPDUGuard, BPDUFilter, RootGuard
and the LoopGuard.
That’s
the last session of this Spanning Tree Module, now in
our upcoming module we will discuss about VLAN’s
If You Like the Post. Don’t forget
to “Subscribe/Share/Comment”. Thank You.




























0 comments:
Post a Comment